You can connect your ISMS.online (IO) platform to a Microsoft Entra tenant through a Project in IO.
Once enabled, this integration allows you to display user authentication data from Entra within your Projects — for example, linking to relevant access-related controls such as A.5.15: Access Control under ISO 27001.
Integration Capabilities
The Microsoft Entra integration in ISMS.online can:
Fetch data from Entra showing how many users are MFA Registered and MFA Unregistered.
Display this data as a KPI (Key Performance Indicator) linked to a Control within IO.
This provides valuable insight into how your access control and secure authentication policies are reflected in Entra, helping you understand and evidence how many users in your organisation are using Multi-Factor Authentication (MFA).
What is a MFA registered user in Microsoft Entra?
In Microsoft Entra, Multi-Factor Authentication (MFA) adds an extra layer of security by requiring users to verify their identity with more than one method (for example, a password plus an app or security key).
Each user account in Entra includes an isMFARegistered property:
isMFARegistered = true — the user has registered at least one strong authentication method, such as the Microsoft Authenticator app, a FIDO2 key, or phone-based verification.
isMFARegistered = false — the user has not registered any strong authentication method.
Important: ISMS.online (IO) does not configure or manage MFA settings. All MFA policies and methods are set up and maintained within Microsoft Entra ID by your administrators.
This integration helps you easily see how many users have registered for MFA, giving insight into your organisation’s adoption of secure access controls.
Who can set up the Entra integration?
To add and enable the Entra integration in a Project, you must have:
| Requirement | Description |
|---|---|
| Project Admin Permission | You must be a Project Administrator in IO (you’ll see the Settings tab in the top right of a Project). |
| Entra Administrator Role | Your Microsoft account must have the Global Reader or Security Administrator role within Microsoft Entra ID, with permissions to view user authentication data. |
| Global Admin Approval | A Global Administrator must approve IO’s access to Entra. If you are not a Global Admin, one must complete the approval process in the Microsoft Entra Admin Center → Enterprise Applications. |
Setting up the Intune integration
Open your Project
Navigate to the Project where you want to display Microsoft Entra MFA data.
Example: ISO 27001 Policies & Controls → A.5.15: Access Control.Locate the Activity
Go to the specific Activity where you want to show the Entra data and scroll to the bottom of the Note.
Add a KPI Card
Click + Add next to the KPI heading, then select the Microsoft Entra MFA Registration card.
Enable the Integration
An empty chart will appear in the KPI section.
Hover over the ? tooltip for setup guidance around required permissions.
Click Enable — an authentication window will open.


Approve Access
If you are a Global Admin, you can approve IO’s access immediately.
If you are not a Global Admin, ask one to approve the request via the Microsoft Entra Admin Center.

Confirm Successful Connection
The authentication will succeed if:Access has been approved by a Global Admin, and
Your account has the appropriate permissions in Entra.

Once complete, the integration is active. Data will automatically be fetched per the schedule and displayed in the KPI chart. Hover over the sections of the donut chart to view tooltips showing the number of MFA Registered and Unregistered users detected in Entra. Click the drill through button to see a list of unregistered users.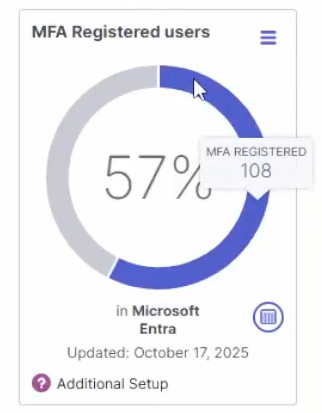
Data Refresh and Timing
- The integration automatically fetches updated data once per day at 13:00 UTC.
- For testing or initial setup, complete the configuration before 13:00 UTC to see your first data refresh on the same day.
- If setup is completed after 13:00 UTC, data will appear following the next scheduled refresh at 13:00 UTC the following day.
